
How Enterprise Browsers Can Make the Workplace More Secure
The world of work is far more fluid and flexible than ever before, with many people working remotely some or all of the time. At the same time, the amount of unstructured data has increased rapidly, and, correspondingly, cyberattacks have increased in frequency, volume and sophistication.
This reality makes it more important than ever for organizations to secure their data. A 2023 IBM report states that the average data breach costs $4.45 million—a 15% increase over three years. But today, protecting critical resources is more difficult than ever, and IT and security teams need to adapt their approach.
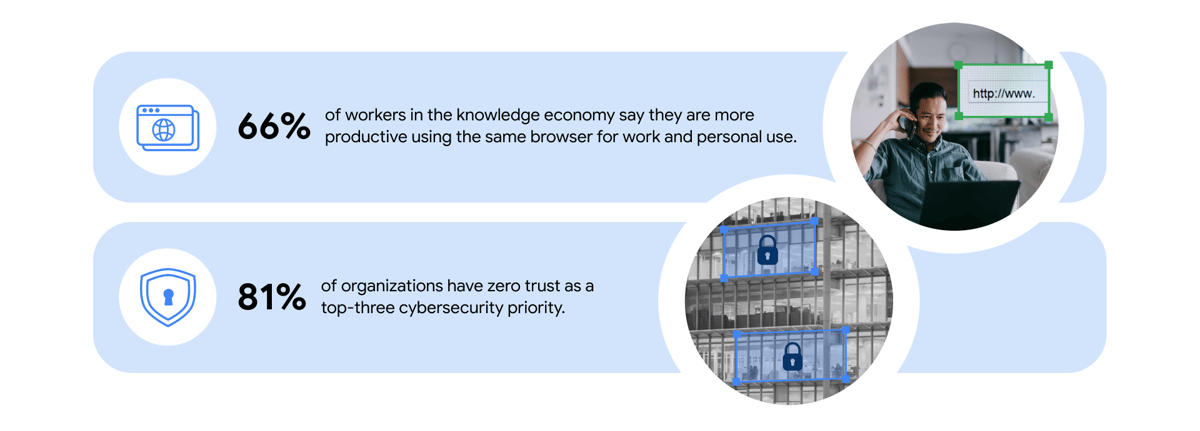
Many workers in the knowledge economy are now doing much of their work on the web and on the go, using their laptops and phones, and they want access to resources to be simple and quick.
“It needs to be responsive, and they need to be able to do their job without waiting on a web page to load, or security blockers stopping them from being productive,” says Diana Lopez, Global Security Solutions Architect at Google Chrome Enterprise.
“Typically, knowledge workers are not thinking about security first,” she points out. “They might not be paying attention to where they are accessing data, or if they accidentally share it outside the company. BYOD [bring your own device] is increasing risk. Most of it is accidental, or succumbing to social engineering in various forms.”
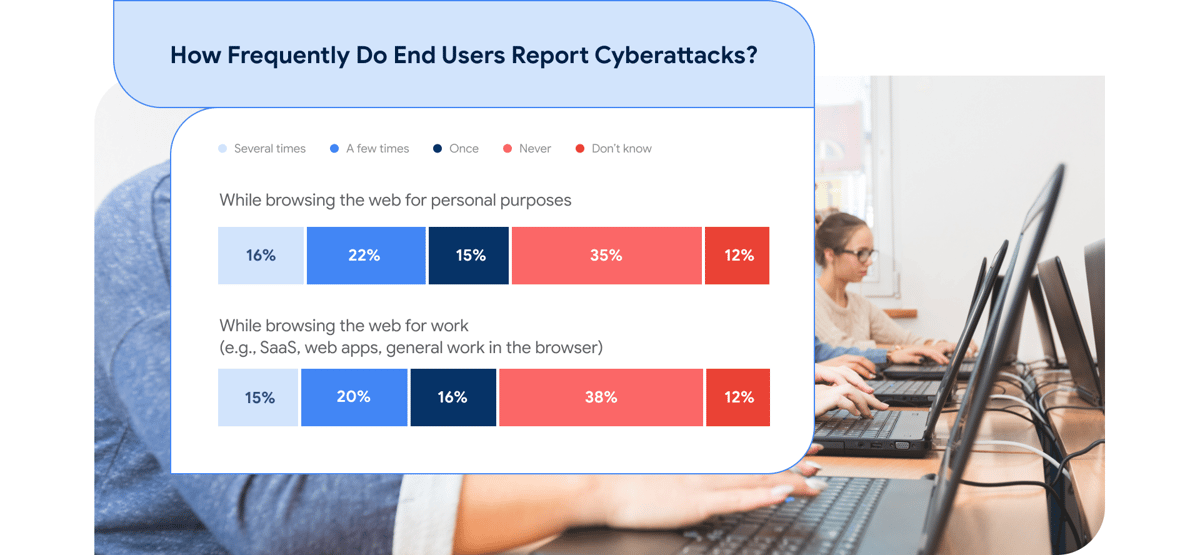
As the risks presented by remote workers grow, companies need to have visibility on what their staff are doing. But making employees install security software on their devices slows down network and resource access, which causes frustration and may lead to unsecured workarounds.

Due to the diminished effectiveness of traditional security solutions, browsers have become increasingly crucial to business, and have emerged as the new destination for secure enterprise activities.
“Before, my desktop was my endpoint; it was where I did all my work,” says Lopez. "The browser used to be just a place to look something up, to get access to data. Now, it is not just a portal to the internet, but the new endpoint where almost every high-value activity or interaction in the enterprise takes place. I do 100% of my day in a browser now.”
In the new cybersecurity model, “you need to secure at the user level,” Lopez says. “No matter what they’re doing, you need to be able to secure where they’re accessing the data.”
Doing this on a browser removes the need for processes such as SSL decryption and the use of proxies. “We’re layering all the security in the actual brains of the browser, rather than having to rely on third-party products to do that,” she explains.
And if everything is done through the browser, organizations using Chrome Enterprise can deploy a centralized enforcement point to control employees’ access.
“If you're a company with 50,000 employees and they're all using Chrome, you can enroll all those Chrome browsers to the Google admin console as a managed device, and get all of these control features in one place," says Lopez. “So, being able to centrally manage all your browsers from one place—that’s going to be the admin console. ”
This centralized view is crucial, because data is structured differently today than it used to be, with much of it sitting in the cloud and not accessible through on-premise corporate systems.

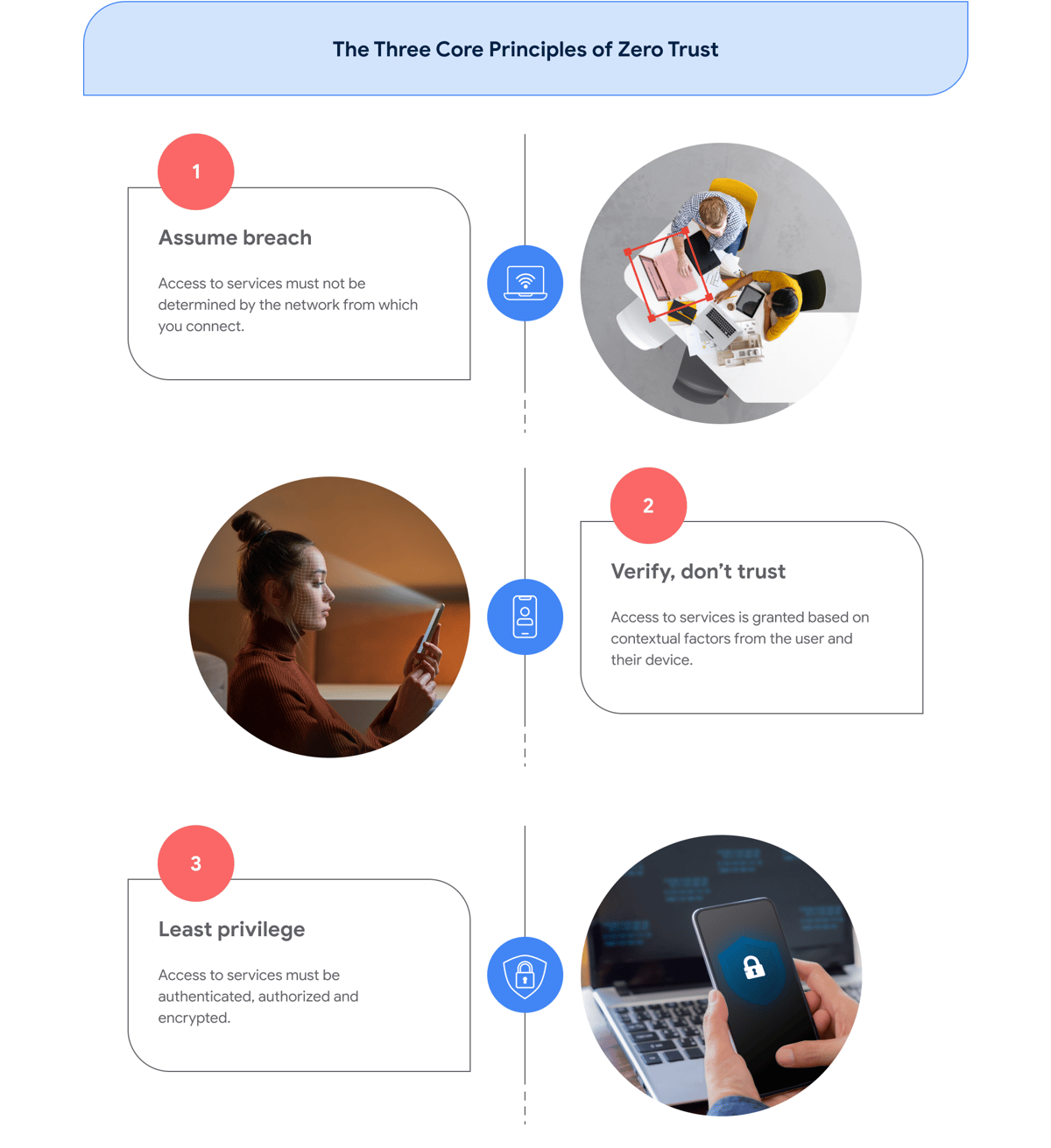
A zero-trust approach is seen as key to keeping data secure in the age of the knowledge economy. The growth in browser use and zero-trust solutions means that businesses looking at enterprise browser technologies should ensure that they can integrate with any zero-trust architecture that they are using. And this architecture should follow three core principles: Watch your supply chain; deploy identity and access management; and monitor your assets.
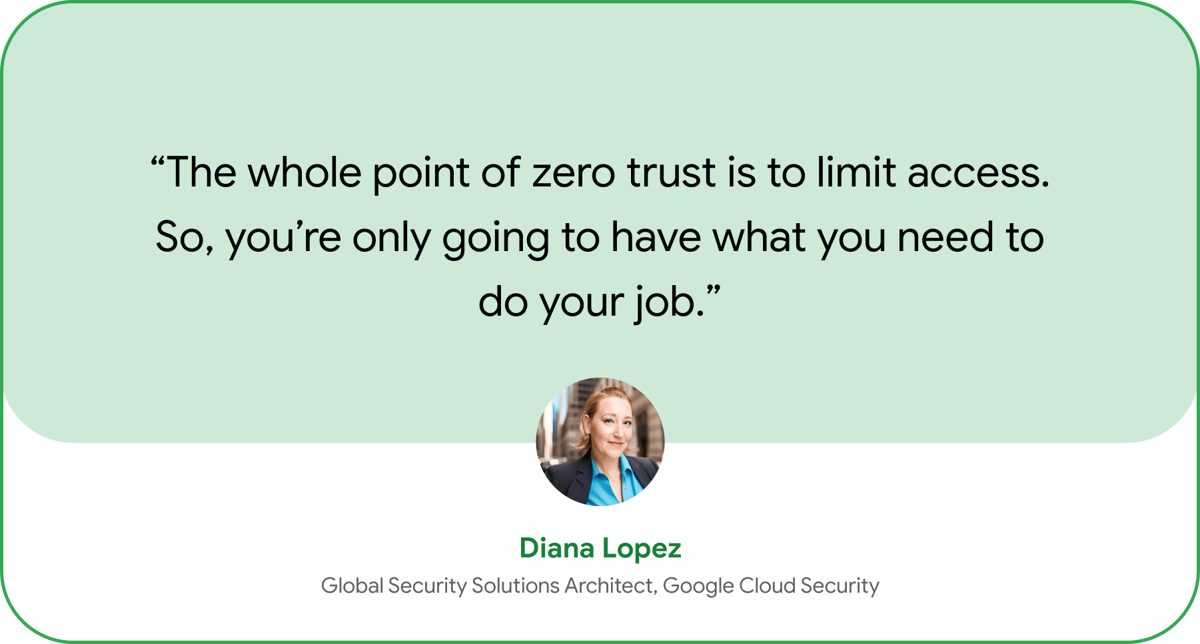
Lopez says that “the whole point of zero trust is least privilege access. So, you’re only going to have what you need to do your job.” This could involve, for example, ensuring that users can only log into work applications from their work computers rather than their own devices, while allowing them to use BYOD for email. “It’s about making sure you have the controls in place to differentiate what is actually needed for people to do their job, and not just having wide-open access,” she says.
Google has been using the zero-trust model for a decade; that approach is now the Chrome Enterprise Premium solution, which moves access controls to individual users, enabling secure work from virtually any location without the need for a traditional VPN.
The company has greater visibility when everything is centralized to the browser, and it can ensure that end users can only access secure applications if they follow the correct protocols.
“With Chrome Enterprise, we’re able to provide all the built-in security features that customers get today. But we also have the ability to bring threat intelligence into the browser, through Chrome Enterprise Premium” says Lopez.
