It’s Time to Move Beyond Traditional VPNs
Protect your data and resources from modern threats with a zero trust approach
On any given day, millions of employees connect remotely to their workplaces, signing in from home offices, coffee shops, airport lounges and commuter trains. Forty percent of organizations now rely on virtual private networks (VPNs) to forge these connections, according to Statista. But despite their popularity, legacy VPNs and traditional hub-and-spoke security models are showing diminishing effectiveness against the escalating threats that accompany our cloud- and mobile-first reality.
With VPNs, it’s next to impossible for security teams to effectively protect the perimeter in what has become a perimeter-less landscape, as such outdated network access tools lack visibility into the apps, workloads and devices that must be secured across this growing attack surface, says Ashish Jain, Principal Group Product Manager of Identity and Network Access at Microsoft.
Because VPNs give connected users and devices complete access to an entire corporate network, anyone who signs in can move laterally without limitations. If a bad actor is able to compromise an employee’s credentials, they can easily gain access to a company’s private applications and resources.

As a result of this risk, security leaders are increasingly transitioning away from outdated VPN tools toward zero trust network access (ZTNA) solutions, which remove implicit trust and require strong authentication and continuous verification for users to access company apps and data.
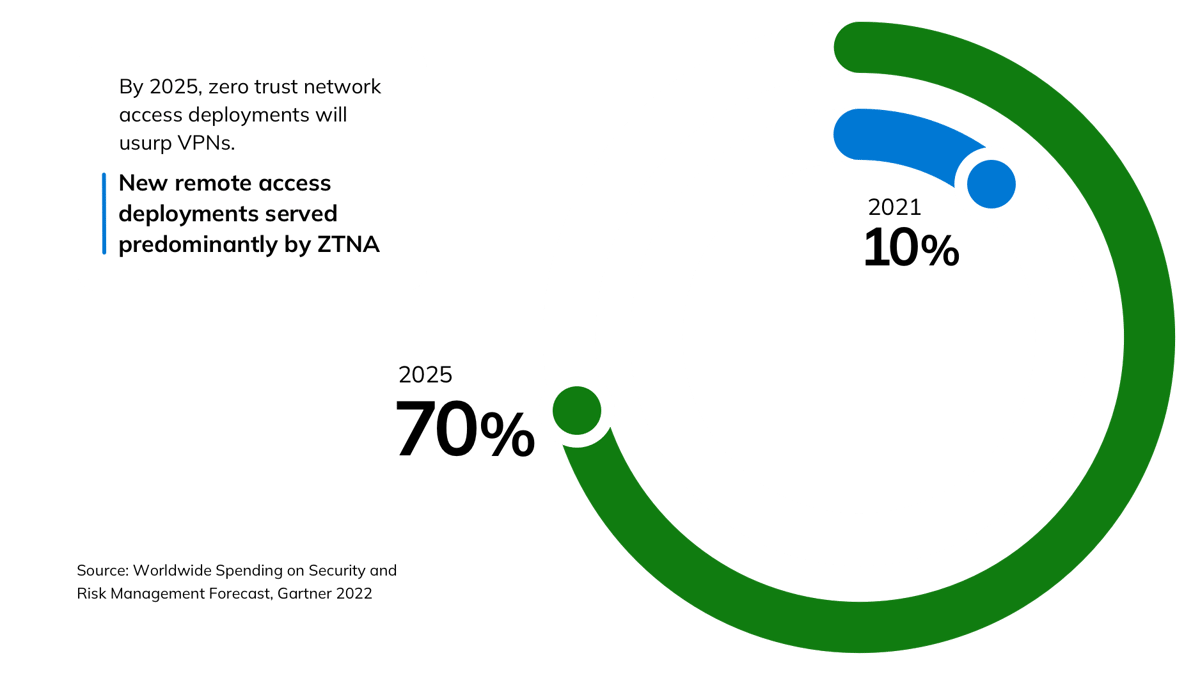
Unlike traditional VPNs, ZTNA limits access to only the apps and resources an employee needs to do their job. Microsoft’s ZTNA offering, Microsoft Entra Private Access, for example, quickly bolsters organizations’ security stance by identifying and restricting assets—both cloud-based and on-premises—that provide access to an overly broad segment of users. Security teams can further narrow the reach of these resources by layering identity controls into network access. Administrators can, for instance, create a conditional access policy that triggers an action to enforce additional security controls if it appears that an employee’s account has been compromised since their last sign-in, even if their session token—the encrypted cryptographic key that allows a user to access a resource—was stolen after they verified who they are, while they’re still logged in.
Elevating network access security for private resources
The challenge of migrating from VPNs to ZTNA is complicated by the fact that many on-premises applications that organizations still rely on often run on arcane authentication protocols, like NTLM and Kerberos. Modernizing these protocols is traditionally labor-intensive and costly.
While Gartner predicts that cloud spending will outpace traditional IT spending for the first time next year, a majority of organizations still use on-premises infrastructure, underscoring the need to extend ZTNA to resources housed in local data centers.
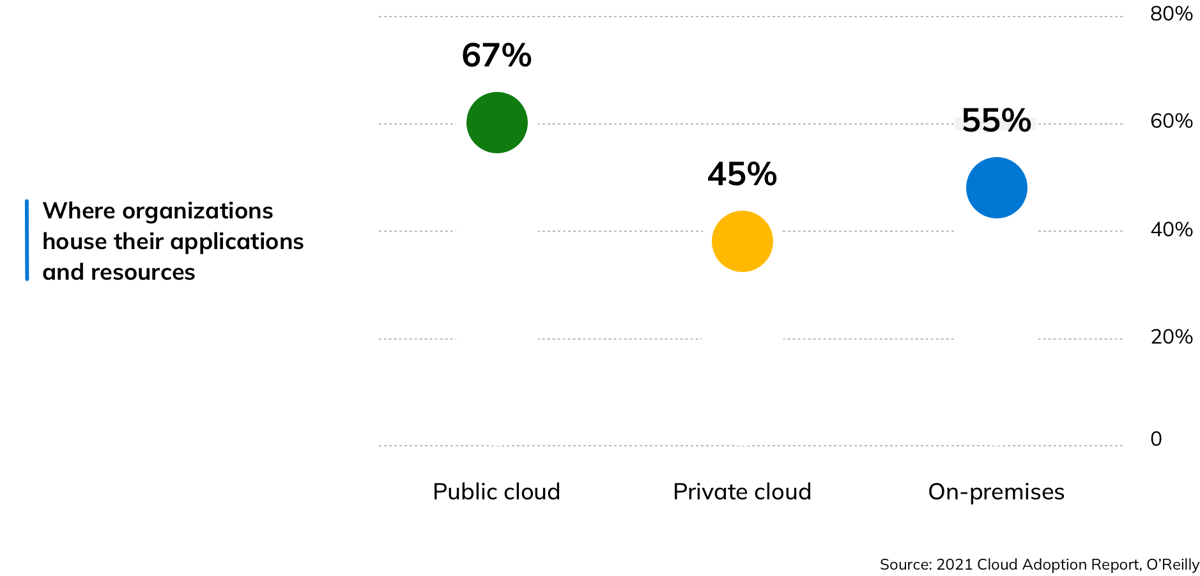
Microsoft Entra Private Access negates the need for a total overhaul of older systems—and VPNs—by extending ZTNA to legacy applications. This transition allows organizations to continue providing access to their existing applications while enhancing security.
“It used to be that the only way for organizations to switch from VPNs was to modernize their applications, which demands a considerable investment,” says Jain. “We give them a choice, so they don’t have to do that.”
Future-proofing your cyber strategy
In order to protect critical resources in today’s hybrid environment, organizations need cyber tools that will mature in step with the evolving threat landscape. Zero trust network access solutions like Microsoft Entra Private Access, which operates on a scalable SaaS platform, are constantly evolving, adding new means for security leaders to control how company networks and private resources are accessed—and allowing them to shore up any gaps before bad actors discover them.
But not all threats come from external sources. Jain says it’s equally important for organizations to protect themselves from insider risks—like a disgruntled employee planting a backdoor before they leave to maintain access to company resources.
Microsoft Entra Private Access operates under the assumption that such a scenario will happen, and safeguards against it by empowering security teams to create policies that grant or deny access based on the widest possible range of factors.
Through advanced application access policies, Jain says that Private Access effectively thwarts unauthorized access “down to the micro level” by using a comprehensive set of access controls, including IP addresses, ports, protocols, fully qualified domain names and wildcards. Soon, the security solution will also give administrators the ability to create policies based on processes running on the user’s device, ensuring that no one is handling data they shouldn’t.
VPNs’ all-or-nothing approach to access—once a cornerstone of network security—is increasingly obsolete in today’s mobile- and cloud-first environment. ZTNA takes a forward-looking stance, giving CISOs the controls necessary to respond to future threats.
“By anticipating attacks before they happen, we give security leaders advanced protection in a cyber landscape that is constantly in flux,” says Jain.
To learn more, visit Microsoft Entra Private Access.
