
Time to Break the Silos Between Identity and Network Security
Reimagine secure access by swapping security silos for a united front
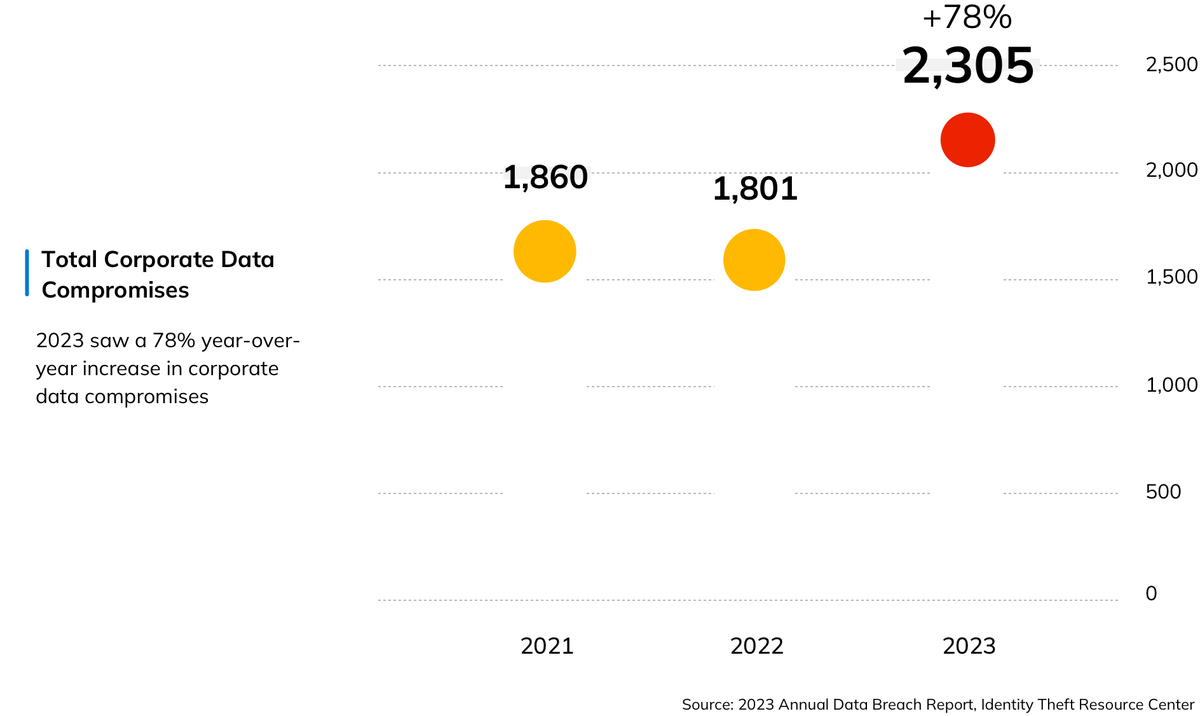
While the advance of hybrid work and cloud computing has allowed businesses to scale, gain efficiencies and cut costs at lightning speed, these same technologies have also been a magnet for cybercriminals, whose cost to businesses exceeded $8 trillion in 2023. The newest tool in their belt? Generative AI. Using readily available large language models, even novice scammers can write malware code, identify network vulnerabilities using dark-web versions of popular gen AI apps and churn out thousands of phishing emails in seconds.
As employees are inundated by phishing, malware and a range of other attacks that target identities and aim to steal user credentials, there is an increased risk that threat actors will successfully compromise login credentials or a personal device to gain access to a company’s remote network. Once they’re in, these cybercriminals can move laterally throughout the network, take advantage of privilege creep and exfiltrate sensitive data.
The newfound ease with which hackers can compromise an employee’s device also underscores how traditional network security strategies are falling short in today’s changing digital landscape. Traditionally, network security and identity teams—as well as the tools they use—operate in silos, which makes it harder to comprehensively protect access. By unifying these separate elements, CISOs and their security teams can bolster their security stance in the face of emerging threats.
Bridging the gap between identity and network access controls
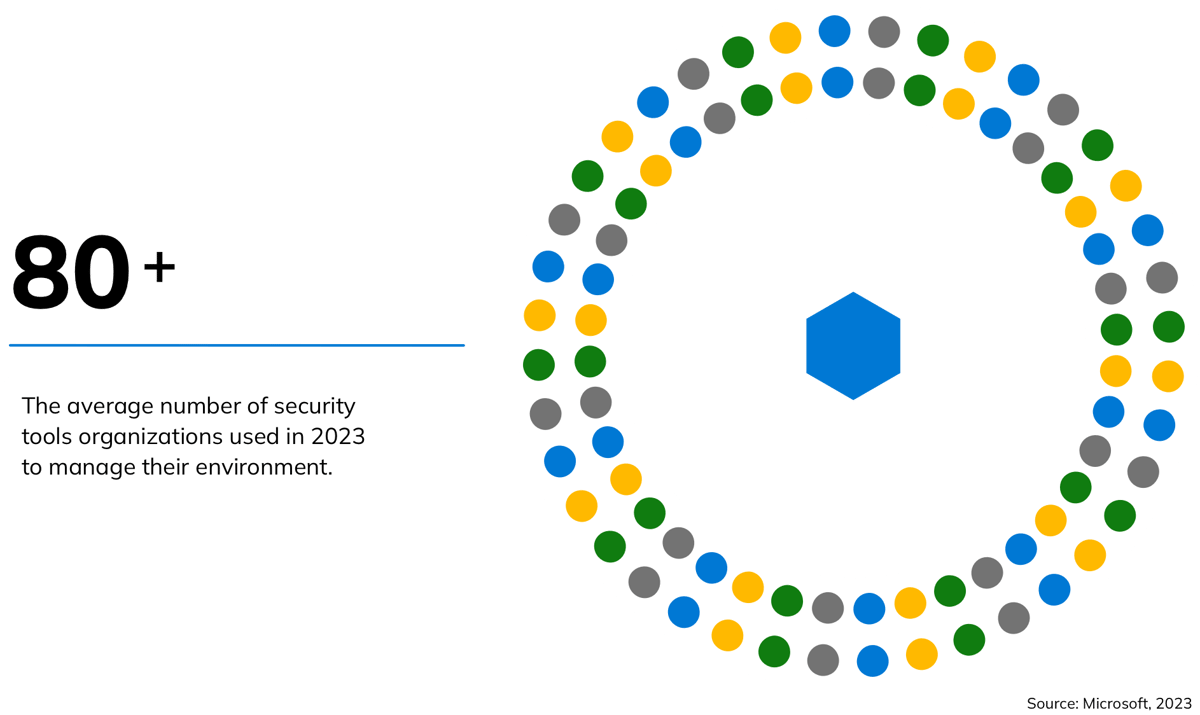
As cybercrime grows more sophisticated, enterprises depend on a growing number of network access and identity management tools from multiple vendors, including single sign-on, multifactor authentication (MFA), identity governance, firewalls, secure web gateways, VPNs and data loss prevention systems. Like the teams that deploy them, these tools are rarely integrated.
Sinead O’Donovan, Vice President of Product Management, Identity and Network Access at Microsoft, points out that in this fragmented, multi-tool environment, these disparate teams are operating in a vacuum when creating the policies that determine who can access different types of resources, from applications to a company’s digital infrastructure.
While each team makes critical access decisions and manages access policies, they rarely check in with each other. This lack of communication between teams can result in policies that overlap, cancel each other out or simply fail to cover critical vulnerabilities. This policy gap can result in security loopholes that bad actors can exploit. For example, if a critical on-premises resource has not been connected to a cloud identity solution—and protected with MFA with granular access permissions—anyone who gains access to a network would also have access to this critical resource.

O’Donovan advises tech leaders to consolidate their disparate policy engines under a single, centralized access policy engine that operates across the entire application landscape. Under a comprehensive single portal, CISOs have the complete view necessary to make informed security decisions, and security teams have what she refers to as a “single pane of glass,” making it easier to collaborate.
Microsoft has built out that single pane with conditional access, a pivotal capability of Microsoft Entra ID that allows security teams to collaborate and easily manage granular identity and network access policies in one place. These policies are enabled by the convergence of Microsoft Entra ID with Microsoft’s security service edge (SSE) solution, which includes two new offerings—Microsoft Entra Internet Access and Microsoft Entra Private Access—that together help teams eliminate gaps in defenses and reduce operational complexities.
Private Access applies identity-centric security controls to all of an organization’s private applications and resources—from file transfer protocol apps to remote desktops—with simplified security policies that can be customized to verify the user, the health of their device and their network. Internet Access, on the other hand, offers security professionals an identity-centric secure web gateway to protect all their internet resources, as well as Microsoft 365 and third-party SaaS apps.
O’Donovan says that a centralized policy engine empowers CISOs with the ability to enforce granular controls that consider identity, device, application and network conditions with any application or website. Security teams can, for example, protect against malicious internet traffic by blocking all devices that lack the latest security updates from accessing external web pages. This ability to enact policies at scale allows CISOs to improve their organizations’ security postures without investing extra resources.
Eliminating silos and embracing zero trust strategy
Preventing breaches is only part of the battle, says O’Donovan, who adds that sooner or later, a malicious actor may find a way into a company’s network using a pernicious new technique.
Microsoft’s SSE solutions make it harder for bad actors to gain access to sensitive data—even if they successfully infiltrate a network—by extending identity protection and access governance to the network access layer, ensuring that users can only access the resources they need to do their jobs. By connecting with the larger Microsoft security portfolio through integrations and an open partner ecosystem, Microsoft’s SSE solution also makes it easier for enterprises to integrate zero trust principles into their entire security environment.
“By doing some housecleaning of their security landscape, companies can reduce all those holes and gaps that they are being exposed to—and just don’t know they’re being exposed to,” O’Donovan says.
To learn more, visit Microsoft Entra Internet Access and Microsoft Entra Private Access.
