
The New Wave of Cyber Threats Is Targeting the Hybrid Work Model
An innovative cybersecurity solution from Microsoft helps workers securely access external resources while improving user productivity
Today’s workplace is not confined by four walls, and teams are often geographically dispersed across different time zones, regions or countries. They communicate, collaborate and innovate using a variety of apps, even within the most traditional sectors. Consequently, organizations have increasingly adopted flexible work-life integration practices, allowing individuals to balance the demands of their professional and personal lives.
The hybrid work model and the flexibility it brings has many potential benefits, from increased productivity to better work-life balance. But moving from a centralized office to a work-from-anywhere model can further blur the boundaries between work-related tasks and personal internet and app usage.
This blurring can create new cybersecurity vulnerabilities and more opportunities for hackers to deploy a broad repertoire of cyberattacks, including adversary-in-the-middle (AitM) attacks—where bad actors eavesdrop on sensitive data—phishing attacks, malware and trojan software, social engineering attacks and advanced persistent threats (APTs)—prolonged attacks in which an intruder gains access to a network and stays there undetected for an extended period of time.
It’s easy to imagine an employee shopping online or checking out links on social media during a virtual company meeting, or making a wager on the big game from their work laptop. Most of these mistakes may be wholly inadvertent, but they open up new avenues for phishing attacks through malicious websites, access token thefts and other serious cyber threats. Some actions, like gambling online or participating in certain online communities, may also introduce reputational risks to the entire organization.
The same risks apply for websites and apps—both sanctioned and unsanctioned—that employees use for work. Often, attackers only need one compromised user or endpoint to move laterally through an organization’s network, cause damage and exfiltrate sensitive data.
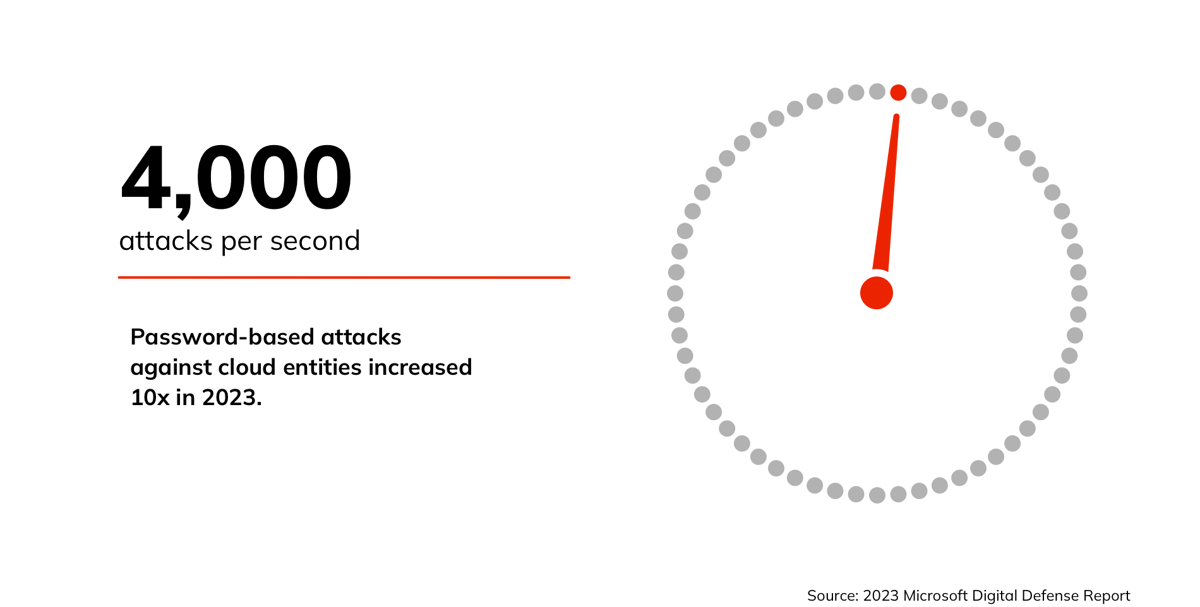
Every time an employee toggles between their work email and personal applications, or checks social media or visits a non-work website or message board on a work device, cybercriminals see an opportunity to insert malicious links, build legitimate-looking phishing sites and exploit malware to launch ransomware and other data-exfiltration attacks.
Ransomware payments exceeded $1 billion for the first time in 2023, according to Chainalysis, and the Anti-Phishing Working Group ranks last year as the worst on record for phishing attacks.
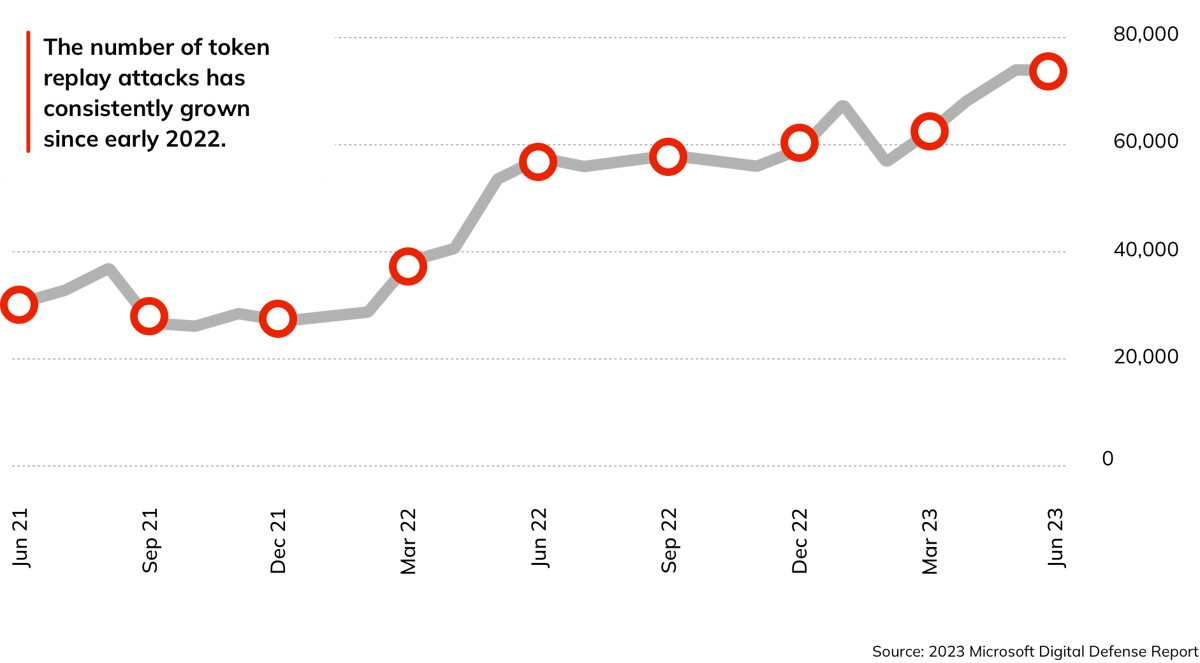
In addition to battling the record-breaking spike in traditional cyberattacks, security teams must ward off new, more sophisticated threats like token replay attacks, where attackers go beyond compromising user credentials and utilize token theft for the purpose of getting into organizations’ environments. The number of token replay attacks has grown since the start of 2022, and has doubled in the last 12 months.
Attackers use two common techniques for token theft:
1. AitM attacks, where adversaries intercept the communication between two or more devices on a network by inserting malicious infrastructure between the user and the legitimate application the user is trying to access. When the user is phished, the malicious infrastructure captures both the credentials of the user and the token.
2. Pass-the-cookie attacks, where an attacker bypasses authentication controls by compromising browser cookies.
In each case, the stolen token can be used to gain access to corporate applications, bypassing traditional access controls like multifactor authentication.
These newer attack strategies and methods are thriving in the absence of collaboration between network access and identity security teams, as traditional security methods have not scaled with the rapidly evolving threat landscape. Armed with a stolen password or session token, a bad actor can easily impersonate a legitimate user and access critical data and resources. Similarly, someone eavesdropping on network communications can bypass or compromise identity security protocols.
To counteract these sophisticated threats, it’s essential for security leaders to foster collaboration between their network and identity teams. An integrated solution that unifies network and identity security can effectively bridge security gaps, protect users and devices, enhance threat detection and defend against evolving threats and attacks.
Collaboration is the best defense against emerging cyber threats
Security professionals need to ensure that employees and vendors can easily and securely access the resources they need to do their jobs without falling victim to hidden internet threats.
Preventing today’s increasingly sophisticated cyberattacks demands that organizations use a combination of security tools that work in concert to provide an in-depth defense, says Anupma Sharma, Principal Group Product Manager at Microsoft.

Security silos are most often the result of organizational inertia. Changing the way we work usually happens even more slowly than modernizing the technology we use. Most security teams implemented their organization’s safeguards during the pre-digital transformation era, when networking teams focused on infrastructure and relied on on-premises solutions and hub-and-spoke network security models.
Under this legacy framework, network access and identity security teams and tools often work separately and lack coordination in their strategies to protect users’ access to company resources. Today, it’s clear that traditional technologies and siloed approaches don’t scale to protect against novel cyber techniques.
Sharma says that by working as a “split brain,” each team commonly crafts separate policies to address advancing threats, which creates security gaps that cybercriminals can exploit.
For example, if network access is granted without contextual information around a user’s identity—like whether the device they’re using to enter the network is still healthy—there’s little to stop a bad actor from infiltrating a company network, then moving laterally in search of sensitive information. Also, if organizations don’t apply identity controls to external apps and websites, employees are at much greater risk of sharing credentials and sensitive data with bad actors.
To close these gaps, security teams need an identity-centric secure web gateway solution that:
1. Gives security leaders end-to-end visibility across their entire environment, no matter where the users are connecting from or where the apps and resources are located.
2. Enforces adaptive conditional access controls at scale, so security professionals can verify that a user’s device is healthy, that their sign-in risk is acceptable and that their location is familiar before granting access to company applications and resources.
3. Combines context-aware access with traditional web content filtering, so users don’t accidentally introduce something unsafe into a company’s network.
Microsoft Entra Internet Access, part of Microsoft’s security service edge (SSE) offering, uses an identity-centric web gateway to secure access to all internet and SaaS applications and resources. Built on zero-trust principles, this comprehensive security solution protects organizations against internet threats, malicious network traffic and unsafe content.
By unifying access controls under a single policy engine, Microsoft Entra Internet Access protects workers and their devices from internet threats, while safeguarding the company resources they need to do their jobs.
Helping employees be more productive and safer online
Another major challenge to organizations is the high number of unsanctioned apps that employees use to try and make their jobs easier; as a result, workers may share sensitive information outside of the corporate network. This practice can put employee and company data at risk.
According to Sharma, IT administrators routinely underestimate how many cloud apps their employees use. To minimize the threat of “shadow IT”—tech deployed without the knowledge of security teams—she recommends that organizations gain visibility over unsanctioned apps in order to better protect employees and the enterprise.

Microsoft Defender for Cloud Apps, which integrates with Microsoft Entra, provides security teams with a bird’s-eye view of the entire app landscape.
To protect employees from unwittingly visiting malicious websites and using suspect apps, Microsoft Entra Internet Access includes web content filtering, a cloud firewall and threat protection. Combined, these tools give security teams greater control over their attack surface, allowing them to reduce lateral threat movement by restricting access based on predefined criteria, such as the IP address, port or protocol being used to gain access.
Because malicious actors are quickly advancing their techniques, Internet Access has an agile roadmap of security features that address evolving threats. The compliant network feature, for example, safeguards against sophisticated attacks like token theft by ensuring that all user traffic flows through Microsoft’s secured network boundaries, maintaining network integrity when accessing vital resources.
As technology advances and organizations adopt generative AI, leading to a more connected workforce, the separation between work and personal life is likely to diminish further—and cybercriminals will continue to look for ways to take advantage of this blurring line.
To keep employees and company resources safe, security leaders need a unified solution that safeguards the critical resources and tools that the workforce relies on.
“Productivity shouldn’t come at the cost of security,” says Sharma. “Microsoft’s unique advantage is that we take that tension away, so employees can focus on their work without worrying about online threats.”
To learn more, visit Microsoft Entra Internet Access.
